How Point of Sale (PoS) Malware Steals Credit Card Data
The Quick Heal Quarterly Threat Report for the second quarter of 2015 indicated a massive rise in the number of malware samples that afflicted the Windows platform across the world. This trend can be attributed to the fact that malware authors have started propagating their malicious software variants to all corners of the globe, and also the fact that a lot of people still operate their PCs without effective antivirus software and with unpatched operating systems and software.
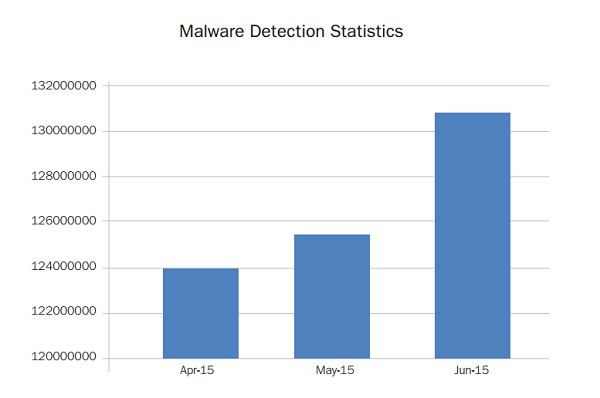
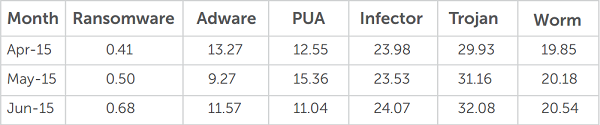
In the months of April, May and June 2015, the Quick Heal Threat Research Labs received many Windows malware samples, and these are highlighted in the complete report which is now available. Moreover, it was also found that a majority of detections occurred on 32-bit machines. This has led us to believe that people looking to buy new machines should consider purchasing 64-bit machines as these have fewer malware threats in proportion.
Some other categories of Windows malware that were detected were found over the following categories:
- Ransomware
- Adware
- Potentially Unwanted Applications (PUAs)
- Infectors
- Trojans
- Worms
- Exploit kits
- Point of Sale (PoS) malware
Key findings of the Quick Heal Threat Report Q2, 2015 for Windows
- Over the Windows platform, Quick Heal detected around 65 million malware samples per month in the second quarter of 2015.
- Moreover, we have found that 74% of Windows malware samples detected run on 32-bit machines. In most cases, these in-the-wild variants are not supported on 64-bit systems.
- In Q2, 2015 the most number of malware threats were detected in the Trojan category. Trojans enter vulnerable machines through trusted software or downloads, or other propagation techniques.
- The most common malware sample detected was LNK.Exploit.Gen, which constituted 26% of the total samples.
- Adware and Malvertising remain top attack vectors for malware authors and malicious software samples. Adware samples are also expected to use browser hijacking techniques in the near future.
- New Point of Sale (PoS) malware families have also been found in Q2 2015 and these steal debit/credit card details from PoS terminals of merchants.
- Threat authors have moved their attention to the banking sector and common banking Trojans are expected to make use of spear phishing emails, social engineering tactics, and RAT (Remote Access Control) tools for remotely controlling ATM machines.
Future trends for Windows malware over the coming months
Adware: Unwanted caretaker
Online ads are getting more personal and the Internet browsing habits of users are under the radar of malware authors. They use this monitoring to deliver ads that carry malicious intent and this process is known as Malvertising. This is done without the consent or knowledge of users and going forward, browser hijacking tricks are going to come under the spotlight. This will enable malware authors to collect personal data and browsing habits of victims more accurately.
Ransomware: More variants, more encryption, more profits
Ransomware has become a very profitable business model for attackers and this trend will continue further. Old ransomware variants are also expected to come back with new modifications. The recent wave of crypto-ransomware samples showcased advanced evasion and encryption tricks and their ability to attack cloud storage services is also expected to take place. Targeting specific industry sectors like banking, healthcare and education is another possible source of income for ransomware writers.
Spamming to continue as an effective infection vector
Most of the ransomware variants encountered in Q2 2015 spread and propagated via spam emails and had improved security evasion and bypass techniques. CryptoWall 3.0 and CRYPVAULT crypto-ransomware are two such ransomware samples that employed noticeable techniques. Such samples are expected to use malicious JavaScript files and complex obfuscation tricks to evade detection from security software. Once done, they will also connect to remote C&C servers and download additional malicious payloads.
More specific banking Trojans
Threat authors have now moved their attention and efforts to the banking sector, as this is a home for money. So, malware families with more advanced techniques are expected to hit machines soon. Spear phishing emails and social engineering tactics can also be used as carriers for delivering banking malware to organizations. The use of RAT (Remote Access Control) tools for remotely controlling ATM machines is also expected to lead to the exposure of sensitive card data.
The Quick Heal Quarterly Threat Report Q2, 2015 goes into the details of the popular malware samples over the Windows platform. The number of samples involved is very large and this is a cause for concern not just for users, but for security service providers as well. This makes the need for security awareness and effective security measures greater than ever.
You can also read about the key highlights of the Android threat report here.