Windows Malware on the Rise – Quick Heal Threat Report Q3 2015
The Quick Heal Threat Research Labs receive malware trends from around the world in real-time and the results these findings show are very insightful. In the third quarter of 2015, the months of July, August and September, the Windows platform has undergone a rather large number of malware attacks and threats. When compared with the previous quarter, Q3 has seen almost a twofold rise in the number of malware samples we have received at the Quick Heal Labs. This blog post highlights some interesting snippets from this data, and the entire details of these samples can be found in the Quick Heal Threat Report – Q3, 2015.
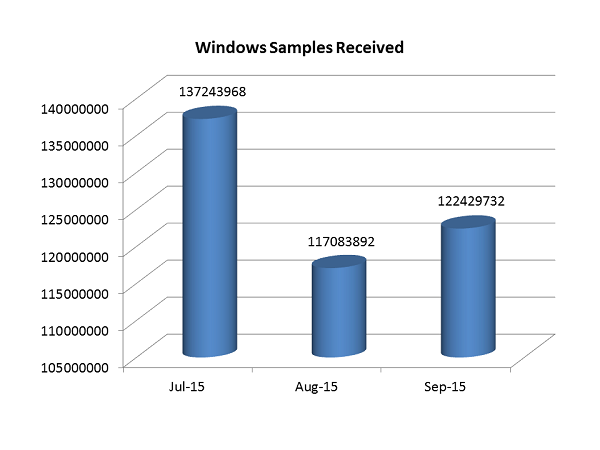
Number of Malware Samples Received by Quick Heal
The detection count of malware samples rose to very high numbers in this quarter and the number of files received by our teams was staggering. Below you can see the number of Windows samples that were received by the Quick Heal Labs.
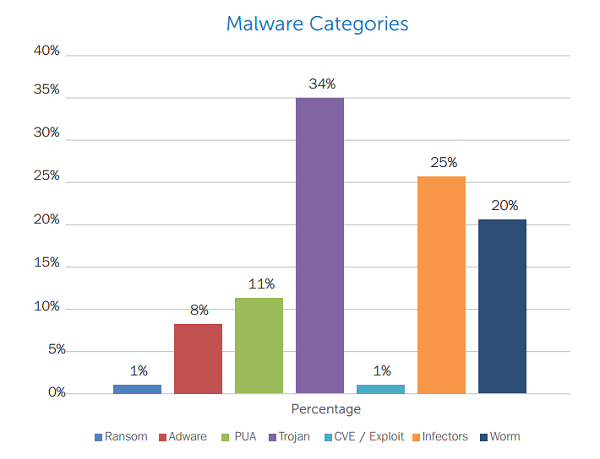
Upon analyzing the samples that have been received, it has been found that Trojans (with 34% share) were the most common type of malware that afflicted the Windows platform over the third quarter of 2015. The other malware types and their distribution is as shown below:
Top 10 Windows Malware
Out of all the samples received, the sample most commonly found was the Worm.Conficker.Gen. This is a self-replicating worm that spreads from machine to machine through USB drives, external hard disks or through file sharing services. It does not need any human interaction to propagate and it also has the ability to disarm security products and other enabled system protections. The top 10 Windows malware samples that were detected in Q3 2015 are as follows:
- Worm.Conficker.Gen
- Browser.MalExt.BF
- JS.Adware.CrossRider.A
- Trojan.BitMin.g8
- PUA.Clientconn.Gen
- Adware.Linkury.A3
- Trojan.Quolko.A
- TrojanDownloader.Esaprof.A4
- PUA.Softonicin.Gen
- TrojanDownloader.Upatre
Apart from these malware samples that were detected, the major Windows malware categories that afflicted hundreds of thousands of machines worldwide were Adware, Ransomware, Exploit Kits and new strains of Banking Malware.
Some prominent Adware samples that were found were CrossRider, Linkury, MultiPlug, Kranet and Eorezo. Ransomware evolved even further and demanded payment from several victims in the form of Bitcoins, an untraceable form of virtual currency. While new strains of Ransomware are rarely discovered anymore, new variants of existing Ransomware samples are found more regularly. Our team discovered new variants of Cryptowall 3.0, Troldesh, TeslaCrypt 2.0, Onion and more previously seen Ransomware types. Apart from these, Exploit Kits that took advantage of security holes in Adobe, Java and other commonly used programs were also found in many machines. Several of these Exploit Kits were used as precursors for larger APT campaigns targeted at industries.
Q3 2015 was an eventful one for Windows malware samples and the number of files that are detected is staggering. It just goes to show the importance of security products and updating software as often as possible. For more details, the in-depth Quick Heal Threat Report Q3, 2015 can be found here.