Evolution of Android Malware – Quick Heal Threat Report Q3 2015
We recently reported the notable Windows malware stats and findings from the Quick Heal Quarterly Threat Report Q3, 2015. In this post we will be sharing some insights and interesting findings from the Android section of this report. As per latest data by IDC, there were close to 350 million active smartphones all around the world in Q2 2015, and around 80% of them ran on Android. That leaves about 280 million open-sourced Android devices (or 3.5% of the world’s total population) open to malware attacks, fake apps, Malvertising, phishing scams and more. In Q3, 2015 the number of files detected by the Quick Heal Threat Research Labs over the Android platform and the nature of malicious files detected has thrown up some surprises, but a few shocks. Here, you can view the detailed Quick Heal Threat Report for Q3, 2015.
Android Malware Samples Received by Quick Heal
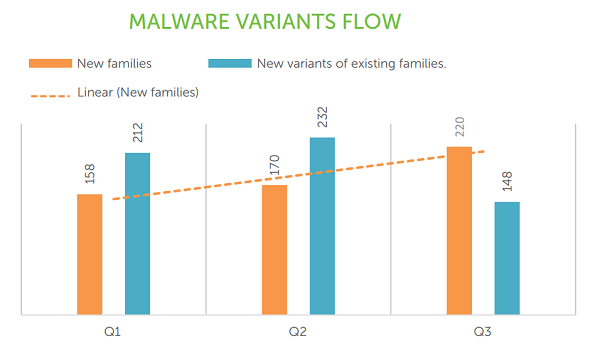
Detection figures of Android samples have exceeded the 1.2 million cumulative mark in the months of July, August and September 2015. In this time period, 220 new families of Android malware have been discovered, and 148 variants of existing families have also been detected. From the graph below, it can also be seen that 500 new Android malware families have been discovered so far in 2015, and over 600 new variants of existing families have also been found.
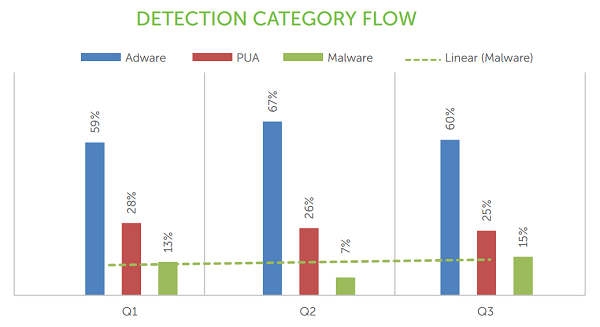
When the Android samples received were broken down further into their categories, the key observation was that Adware constituted two-thirds of all samples received. The details with regards to these can be seen below.
Top 10 Android Malware
Out of all the Android samples received, the most common one was Android.Airpush.G – coming in at 30% of all Android samples. This is an Adware that aggressively pushes ads to the notification bar of compromised devices and adds shortcuts to the homescreen as well. It also modifies device bookmarks and collects and sends various information types to remote servers. The top 10 Android malware samples that were detected in Q3, 2015 are as follows:
- Android.Airpush.G
- Android.Smsreg.DA
- Android.Sprovider.A
- Android.Ztorg.A
- Android.Wroba.A
- Android.Leech.E
- Android.Rootnik.C
- Android.Reaper.A
- Android.CallPay.A
- Android.Senrec.A
Apart from these top 10 Android malware samples, there were other forms of Android malware also discovered that raised alarm bells. Some of these samples were capable of bypassing CAPTCHAS on app stores and hence they could pose as fake apps on legitimate app stores. Some other notable forms of Android malware also had the capability of cloning social networks and games in order to convince people to download the apps.
The Quick Heal Android Threat Report for Q3, 2015 reemphasizes that most of the detected file types and methodologies have been foreseen by security analysts. However, this does not mean that users have been immune from them. It is staggering to see that a large number of people are still running very old Android versions without adequate security solutions installed. So the potential for damage by malware authors is indeed very high. With the in-depth details from the Threat Report, we will be able to delve further into the nature of this malware and the damage it can do with regards to user security and privacy.